The digitalization of the economy has rapidly gained momentum. At the same time, however, the requirements for protection against threats to information security are also increasing. Due to the large number of end devices and, not least, the ever-increasing number of remote workstations and distributed system landscapes, new and effective means of protection are of great importance for minimizing risks. Here we present the most important solutions from our range of services. Customers can book the products directly in our customer portal at https://go.idnt.net. A time limited trial is also available.
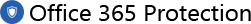
Microsoft Defender for Office 365 helps you protect your organization from malware in file attachments and links in email messages and collaboration programs such as SharePoint, OneDrive and Teams. The solution is not limited to Microsoft 365, but can also be used in conjunction with a hybrid environment.
In particular the component safe links can considerably reduce the risk, especially in connection with phishing messages. This function checks links for malware before they are opened, thus preventing download and alerting the user to the risk. In the case of an unknown download, it is first checked for possible dangers in a so-called "Detonation Chamber" with the help of artificial intelligence before the user can download it.
Administrators have the possibility to control the behavior or to define their own blacklists.
Support is part of our regular Microsoft 365 support agreements.

 For Windows, MacOS, Linux, Android and iOS soon. The agent is already included in Windows.
For Windows, MacOS, Linux, Android and iOS soon. The agent is already included in Windows.With Microsoft Defender for Endpoints, we offer one of the most comprehensive and effective solutions for protecting servers and workstations, which is also optimally suited for mobile devices. It is ideally suited for in-house data centers as well as for the cloud and helps to minimize security risks both preventively and actively in your company.
Real-time detection of vulnerabilities and misconfigurations provides in-depth information on all threats within your organization. Ongoing behavioral analysis and artificial intelligence effectively helps to detect even unknown attacks (zero-day exploits). Using the automation options, you can also react automatically within seconds based on concrete recommendations for action and intelligent decision algorithms.
A connection to all common security management systems and systems for orchestration is also possible. The creation of complex queries is possible via interfaces, which can also be conveniently formulated on the web using the query editor.
We would be happy to provide you with further information or a test option on request.
Whether you have your own IT security team or want our experts to manage it together with your IT, we offer reliable and fair support options for almost any size of business. For more information, please contact our sales department.

With Microsoft Defender for Identity, you can prevent numerous risks that can easily go unnoticed due to common misconfigurations or outdated components within the infrastructure. In addition, user activities and information such as permissions and group memberships or even used protocols and logon attempts are continuously monitored and analyzed to detect anomalies with the help of the built-in artificial intelligence.
With automatic detection and recommended actions, Microsoft Defender for Identity helps drastically reduce countless risks to your business. Seamlessly integrated with Defender for Endpoints, it provides another critical layer of detection and protection against threats to your organization.
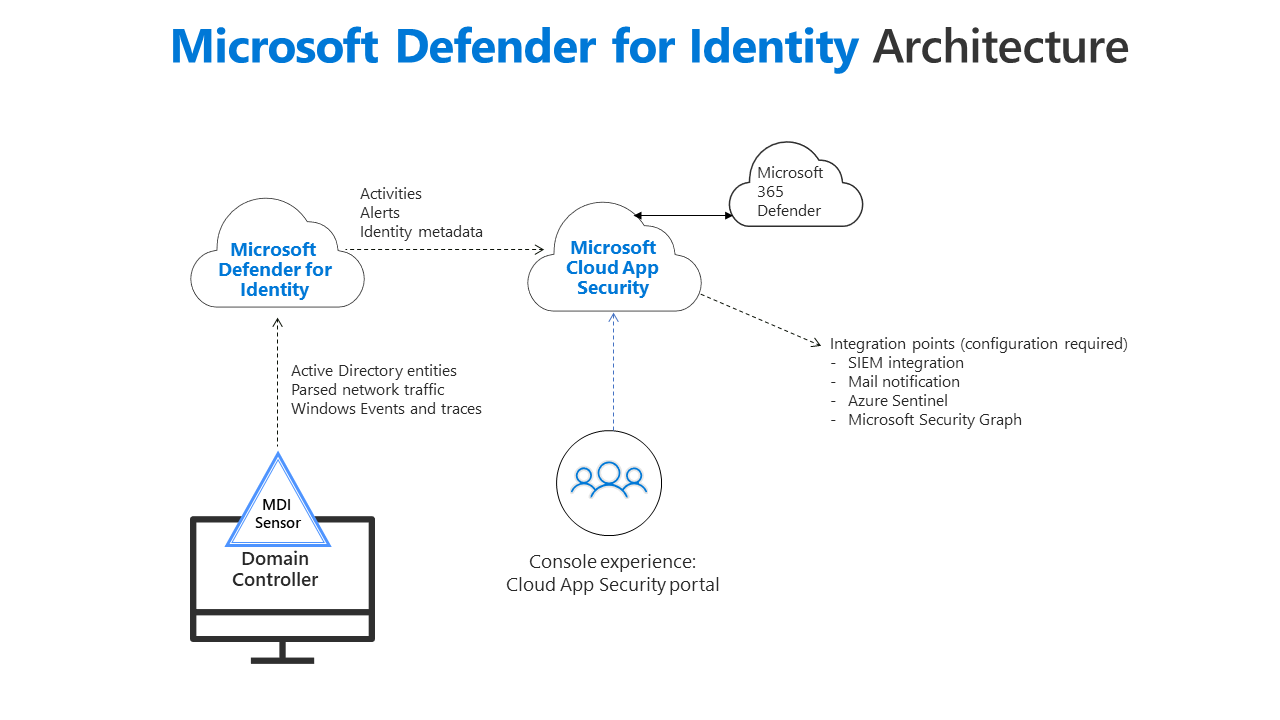
As with Microsoft Defender for Endpoints, we also offer Microsoft Defender for Identity as a self-managed solution, as part of a managed solution, or in shared management with your IT. For more information, please contact our sales department.